AWS Immersion Day with Lacework > Advanced Cloud Security Posture Management (CSPM+) > The Lacework Anomaly Detection
The Lacework Anomaly Detection
In the previous sections, we looked at prevention - identifying issues that make you vulnerable to an attack. Now we will look at Lacework’s anomaly detection events with Polygraph. The Lacework Polygraph analyzes an array of cloud factors to detect breaches. There are currently six Lacework polygraph analysis groups:
- Application/process communications
- Application launches
- Machine communications
- Machine servers
- Privilege changes
- Insider behaviors
- Click on this CloudTrail Dossier that represents malicious activity from an AWS user ec2-user. Anomaly events are detected through Lacework’s Polygraph machine learning technology. Polygraph tracks the user and API activities and detects anomalous and potentially malicious behavior.
- Scroll down to the Polygraph to see a visual representation of the API interactions.
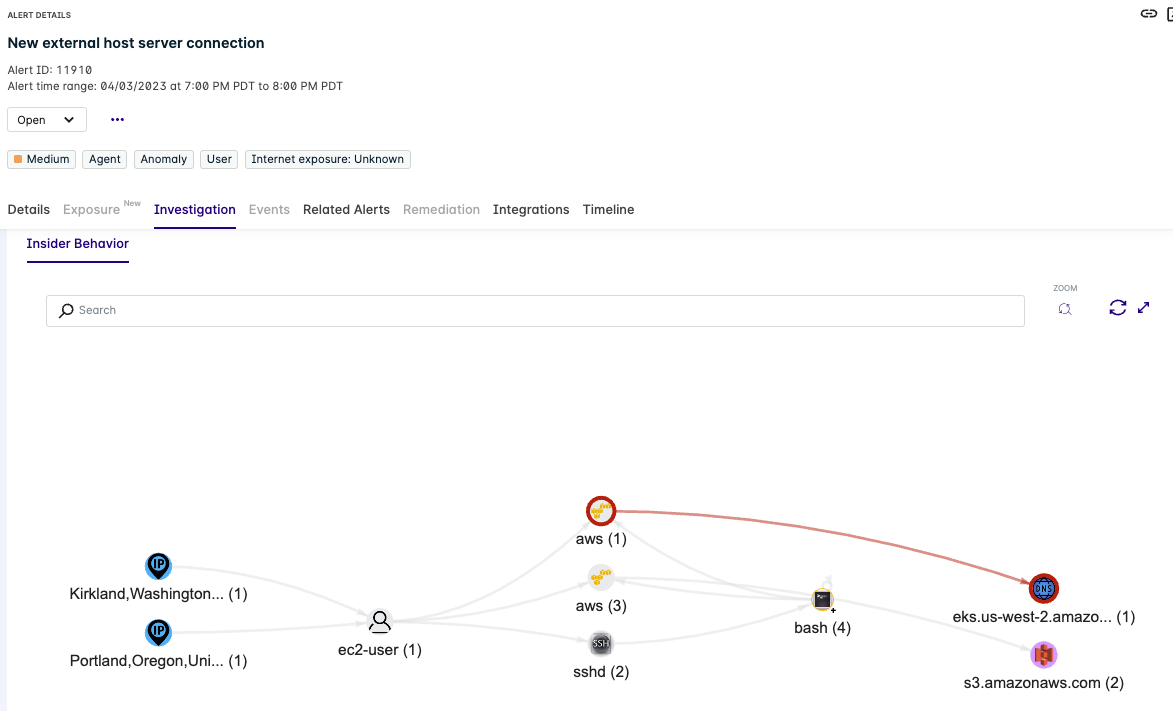
- Hover over ec2-user to and click on the ec2-user link to take us to the user’s activity.
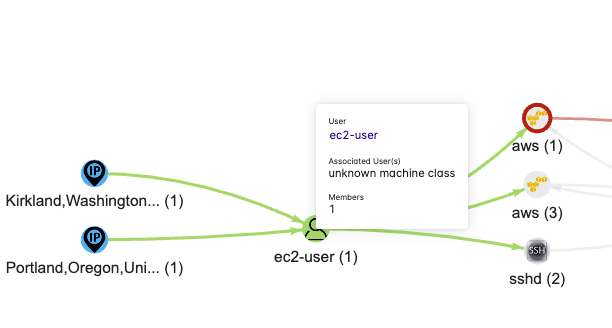
- Scroll down to the Unique Process Details to see what ec2-user was doing.
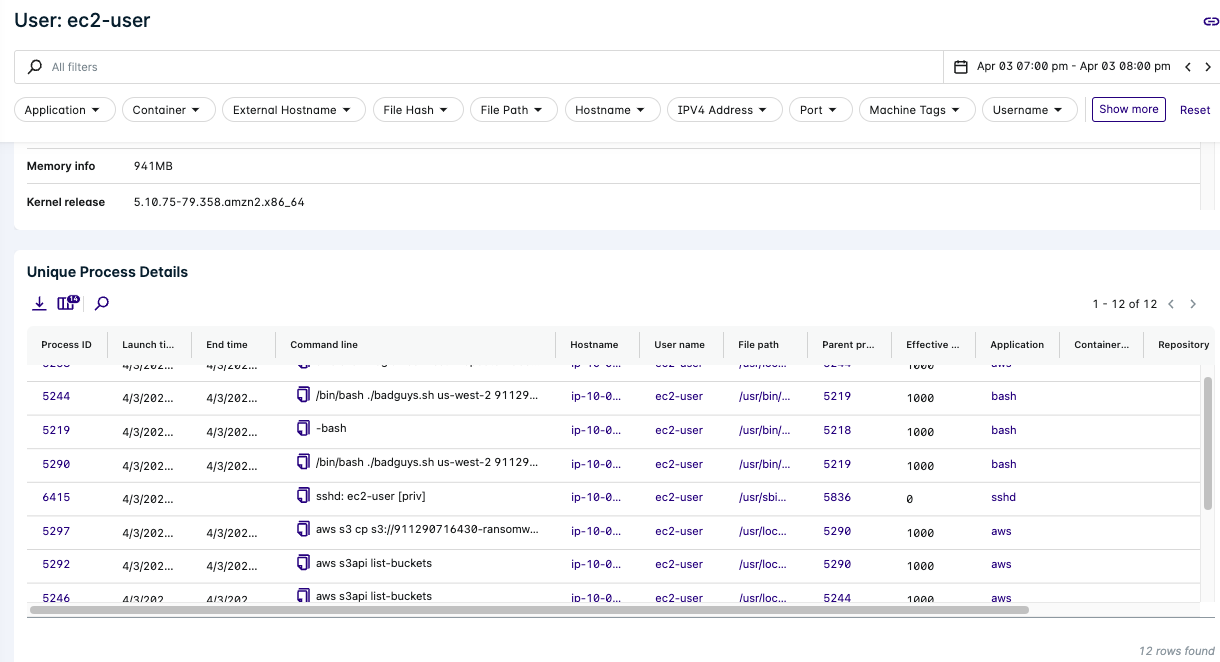
Lacework’s anomaly detection can uncover suspicious activity that may be indicative of a breach. This is a powerful tool for identifying anomalous behavior and can help you quickly identify and respond to threats.