Vulnerabilities
Lacework provides the ability to assess, identify, and report vulnerabilities found on hosts, containers, registries and pods within your environment. This means you can identify and take action on software vulnerabilities in your environment and manage that risk proactively.
Lacework continuously assesses vulnerability risks, identifies OS packages, and correlates them with publicly known vulnerabilities with risk ratings by severity and CVSS scores.
In this section, we will explore container vulnerabilities. Lacework several types of container/image scanning as well as providing runtime protection. Lacework provides similar capabilities for hosts such as EC2 instances.
Lacework provides Public Registry Scanning, Private Registry Scanning, Continuous Integration (CI) Scanning and Local Scanning.
- Select Vulnerabilities > Containers in the Lacework Console. By default, the page displays Fixable and Active vulnerabilities.
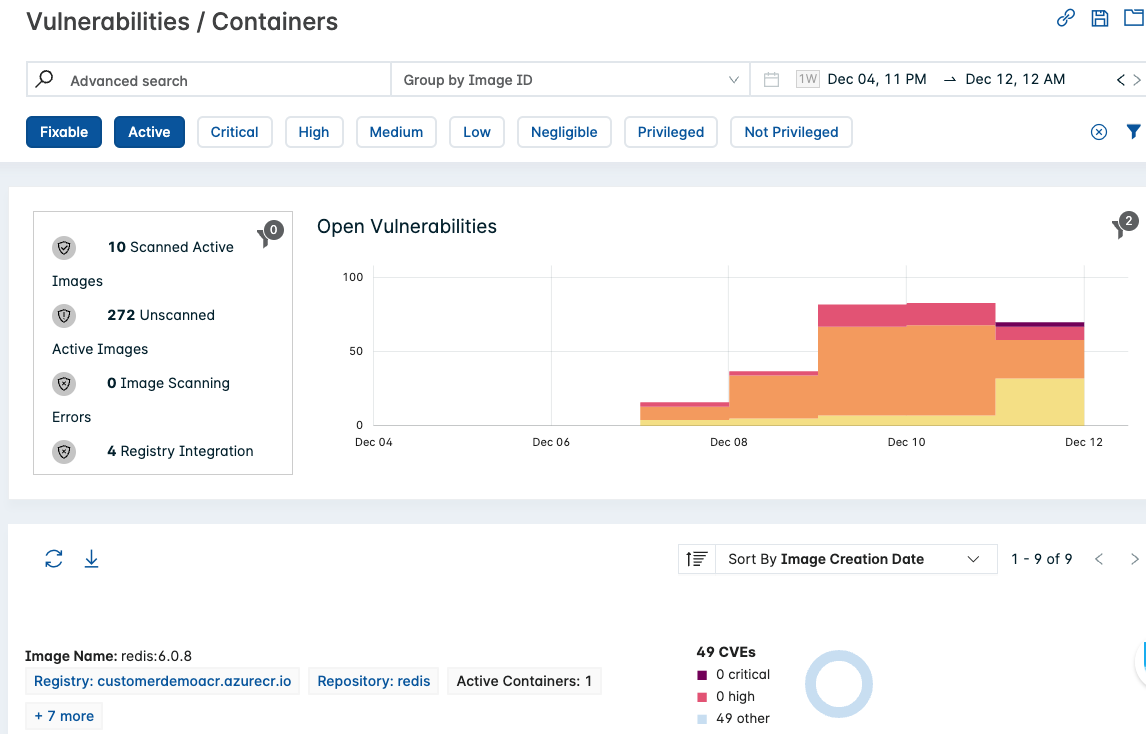
- Observe the Open Vulnerabilities panel. depicts open vulnerabilities. Hover your mouse over the Open Vulnerabilities chart to see the critical, high, medium, and low vulnerabilities.
- View the Vulnerabilties List panel. It shows the list of images with vulnerabilities.
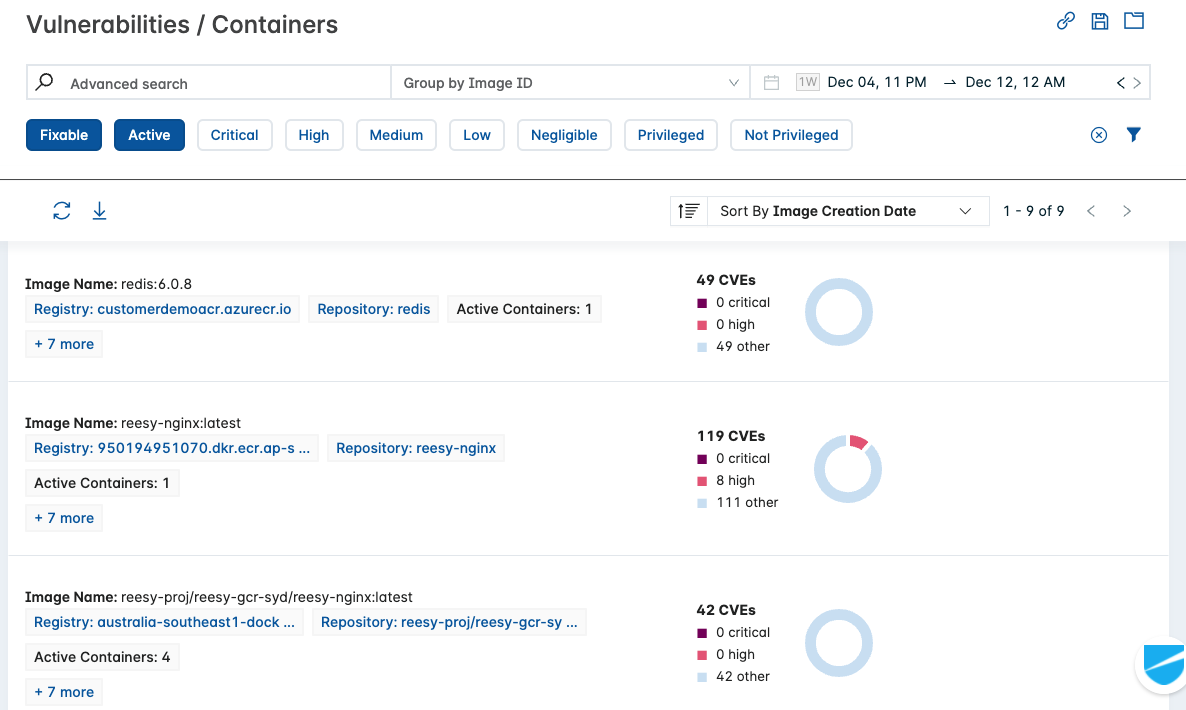
- Click on an image in the list to view the image assessment details.
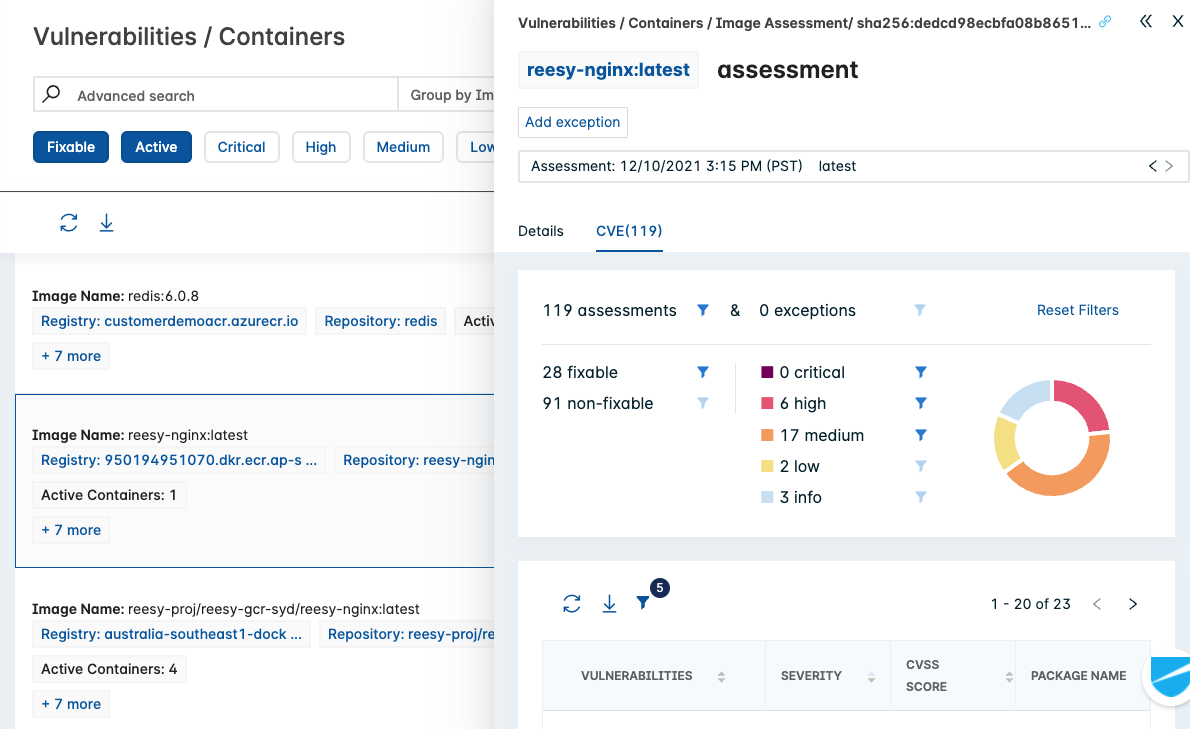
- View the summary and list of CVEs in the CVE tab.
- Click on the Details tab. This provides image details.
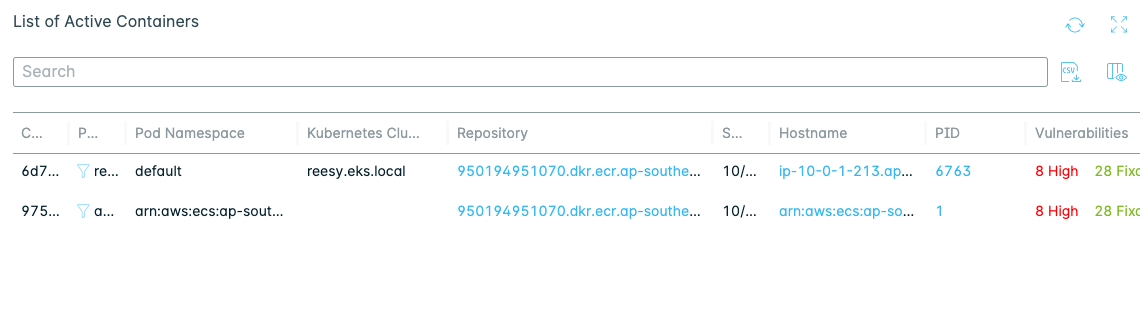
- This image is deployed and is an active container. Scroll down and click on the Active Containers link.
- This Container Dossier provides the details and activity. Scroll down to the List of Active Containers panel to see where the container is deployed.
Lacework’s Container Security features enable you to shift your cloud security left into your software delivery process at multiple stages. You can prevent security vulnerabilities from being deployed.