AWS Immersion Day with Lacework > Advanced Cloud Security Posture Management (CSPM+) > Anatomy of the Attack
Anatomy of the Attack
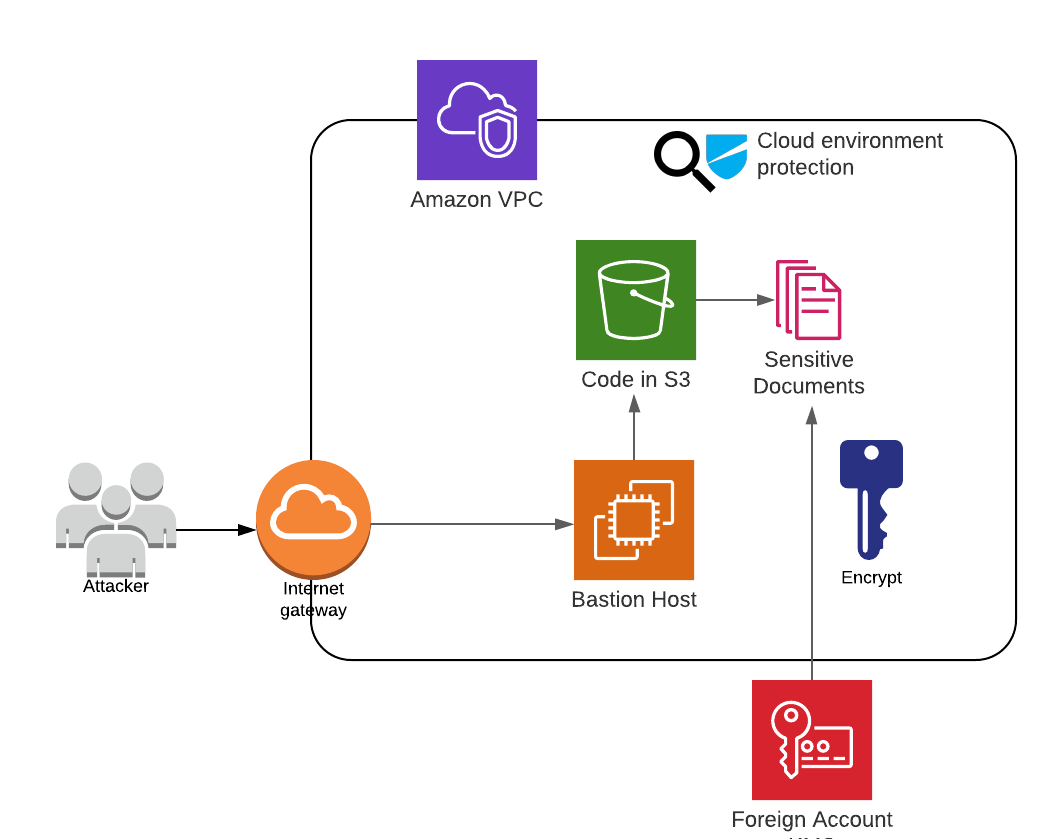
In this scenario, we simulate the typical ransomware actions where an attacker gains access to sensitive data.
- An attacker gains access to a bastion host that is exposed to the internet.
- From the bastion host, the attacker scans for s3 buckets (using the preinstalled AWS CLI).
- The attacker discovers an S3 bucket with sensitive documents.
- The attacker uses encryption keys to encrypt the documents.